In this example I will show you how to setup IIS to require smart card authentication using the DoD Root CA 2, but you can configure IIS to use any trusted root certificate authority.
For this example I am using Windows Server 2012 R2 (IIS 8.5), but these steps should also work for Windows Server 2008 R2 (IIS 7.5).
1. Install Root Certificates
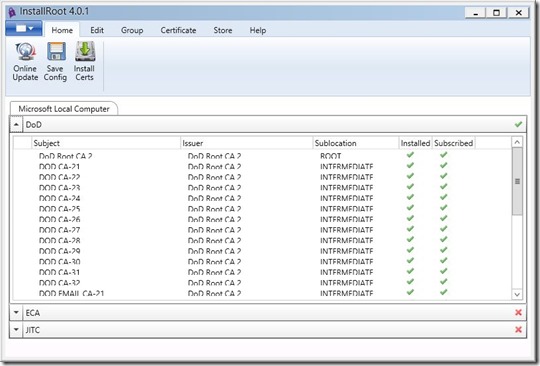
The first step is to ensure you have the root certificates installed for the certificate authority you will authenticate against. For the DoD, we will install them using the “InstallRoot 4” application available at the IASE website: http://iase.disa.mil/pki-pke/.
After the application installs, run “InstallRoot” and click on “Install Certs”. Verify that the DoD certificates are installed and subscribed.
2. Configure the IIS Site for SSL
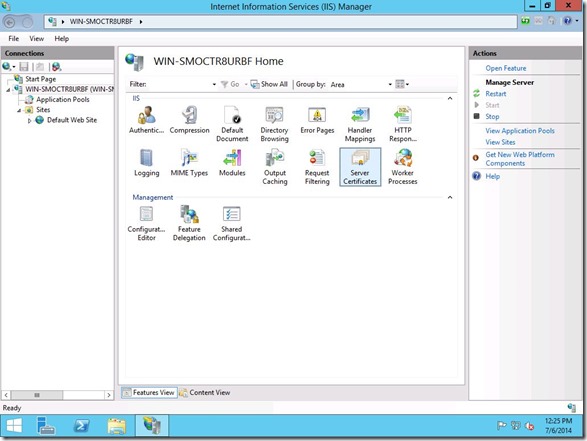
We now need to setup our website to use SSL. For this example, we will create a “self-signed” certificate. In IIS Manager, click on your server and choose “Server Certificates”.
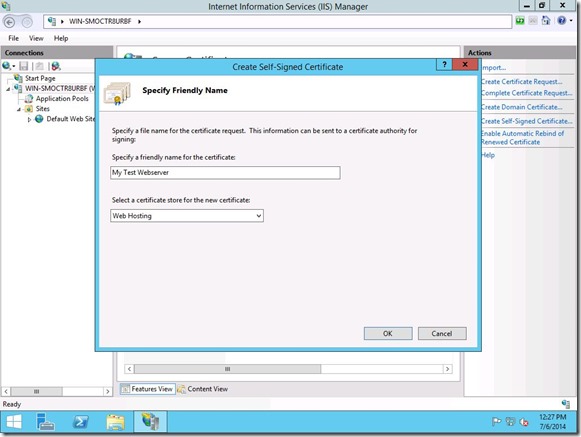
Choose “Create Self-Signed Certificate” for the list on the right. Give your certificate a name and choose “Web Hosting” for the certificate store.
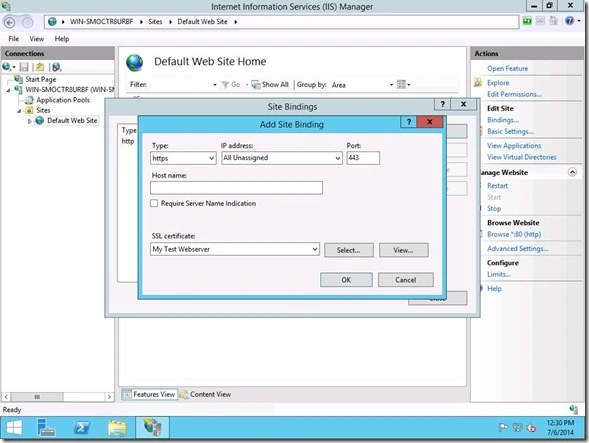
Next we need to bind the certificate to the website. Browse to your website and choose “Bindings”. Select “https” for the “Type” and choose the certificate we created earlier in the “SSL certificate” box.
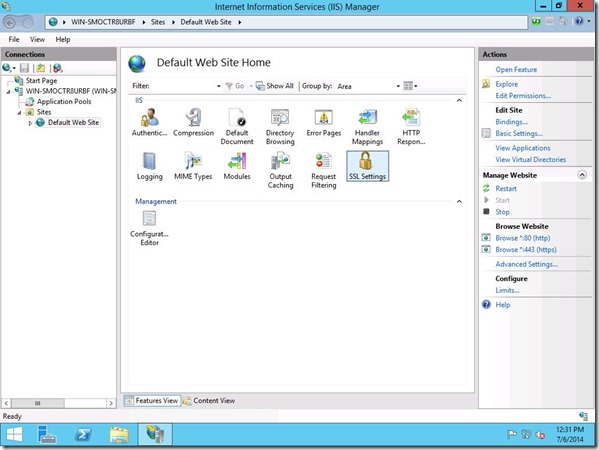
Now choose “SSL Settings”
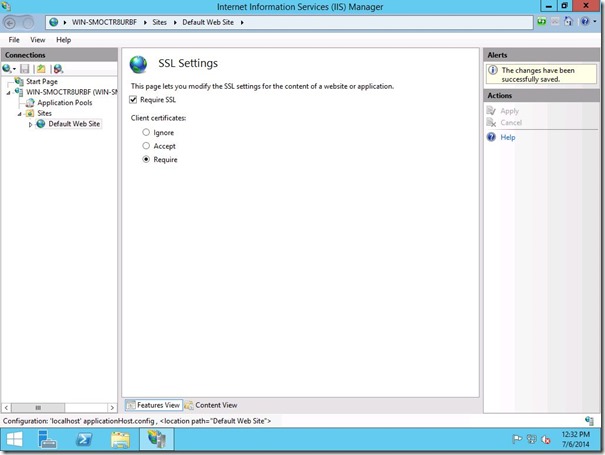
Check “Require SSL” and choose “Require” under “Client certificates”.
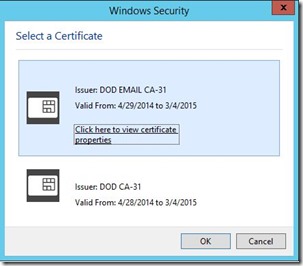
Now when we browse to our website we are prompted for our smart card. Select your certificate and enter your pin and the website now loads.
3. Certificate Trust List
At this point, we verified that our website is able to authenticate using our smart card, but there is a problem. Windows will authenticate any smart card that has a certificate issued by any certificate authority in the servers “Trusted Root Certificate Authority”. In order to limit which certificate authority can authenticate, we need to create a certificate trust list.
To create the Certificate Trust List (CTL) we will use the Microsoft MakeCTL.exe tool. Run this tool on the server “As Administrator” to start the CTL Wizard.
Enter a name for your CTL in the “prefix” box. Click the “Add Purpose” button and enter 1.3.6.1.4.1.311.10.1 for the “Object ID”.
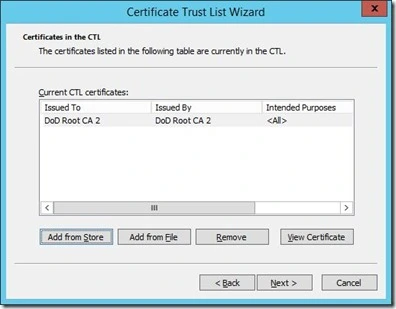
Click “Add from Store” and choose the root certificate authority that you will use for authentication.
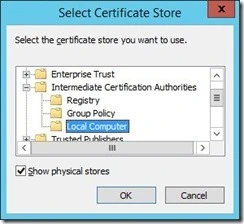
Click “Browse” on “Select Certificate Store” and make sure to check the “Show physical stores” box. Choose “Local Computer” under “Intermediate Certificate Authorities”.
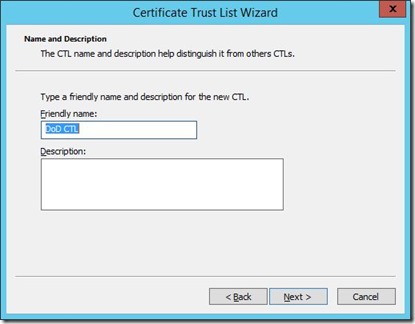
Complete the wizard. Use the same name (prefix) you used in the beginning for the the “Friendly name”.
Now we need to associate the CTL with our website. Start an Administrative Command Prompt and type:
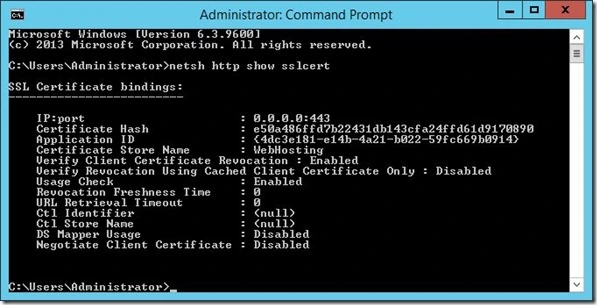
netsh http show sslcert
Note the IP Port, Certificate Hash, and Application ID. We also will need the friendly name of our CTL.
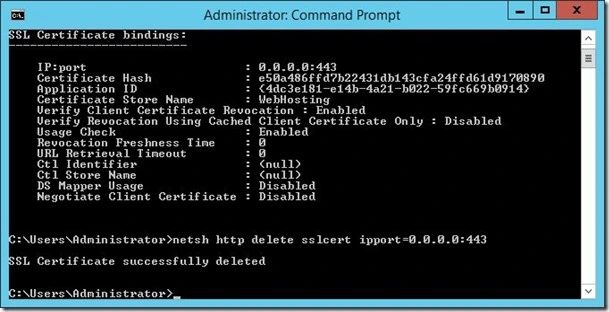
Now we delete the existing SSL binding:
“netsh http delete sslcert ipport=0.0.0.0.:443”
Now add the new binding with the CTL. Replace the ipport, certhash, appid, and sslctlidentifier with your unique configuration.
netsh http add sslcert ipport=0.0.0.0:443 certhash=e50a486ffd7b22431db143cfa24ffd61d9170890 appid={4dc3e181-e14b-4a21-b022-59fc669b0914} sslctlidentifier=”DoD CTL” sslctlstorename=CA
That’s it. Now the site should now only authenticate users who have certificates trusted by certificate authorities listed in the CTL.




Where do we get the MakeCTL.exe tool??
MakeCTL is part of the Windows Server 2003 SP1 Platform SDK. You can download it from Microsoft at http://www.microsoft.com/en-us/download/details.aspx?id=6510.
One note, If you are working with a Windows Server 2008 R2 or newer server, you will need to run this utility from a Windows Server 2003 or 2008 (non-R2) machine and copy over the CTL.
I have applied this to a SharePoint 2010 Foundation Server website on IIS7.5. It’s working but my question is how would I limit access to specific DoD CAC card users. I haven’t found a way to successfully add a CAC user via the SharePoint interface. Any ideas or suggestions?
You would need to use client certificate mapping. There are two types in IIS and these are installed as Role Services. You can read up on it at this blog: http://www.sharepointsecurity.com/sharepoint/sharepoint-security/sharepoint-and-smartcards-cac-cards/
I struggle with standalone WCF SSL server, trying to request certificate from the client. I try to limit the list of acceptabe client certificates the server send back at handshake. With the help of CTL. Still no luck.
I successfully added my CTL to store, linked port and certificate with the help of netsh. But HTTP.sys, which actually do the handhake on the server side, simply ignore my CTL. It send just all server’s CAs. May be I do something wrong? By the way, I have simple Windows 7 machine, not server. I wonder, why in the last “netsh http add sslcert” you don’t use “clientcertnegotiation=enable”?
When I remove the clientcertnegotiation parameter, it simply become disabled, and no acceptable CA names sent at all. Server simply don’t request certificate from the client. Would you be so kind to check the clientcertnegotiation parameter absence necessity?
Both 2003 and 2008 (nonR2) are EOL. Is there an updated solution?
Make sure that when running the netsh command in PowerShell, wrap the appid={4d…14} in quotes so appid='{4d…14}’
Also, if you get a logon session error when running the netsh command, try appending certstorename=WebHosting onto the end.
Also, make sure to add DoD Root CA 3 when creating the CTL since this was originally posted a couple of years ago.
Great explanation and still useful. Thanks for posting!
Good writing. Cheers
Expanding on this scenario, do you have advice on how to configure for an AD site that relies on PIV card with username hint field – and altsecurityIdentities attribute pre-populated with the subject from the CAC card?